I removed the software from my site because it was marked as a "virus" but a lot of people continued to ask me if an updated version was available.
Well, finally it is :-)
Back to the basics. Why should I spoof my address?
I'm assuming you know what a MAC address is. If not, Wikipedia may give you a hint.In the time I talked with people who found very funny and unexpected uses for MacMakeup, hence in the MAC alteration process itself. If you are among them and want to share your idea, just write me.
MAC addresses are a mean to have your device globally unique. I mean on a planetary scale. No two MAC addresses should be the same. So in the time this address was used to uniquely identify your device for licensing or security purposes.
- I recently discovered that TeamViewer seems to use the MAC address to identify your device and decide whether or not you're making "commercial" use of the software. Just google for it.
- Another use of a new MAC address if to make passive fingerprinting/profile building more difficult. Several network software or appliances nowadays try to build "profiles" of network devices. Having layer 2 information is considered (?) more solid than layer 3 addresses that change often, especially when DHCPs are involved.
- Talking about DHCP, they tend to re-assign IPs to known MAC addresses, so you may just need a different IP to test something, despite the DHCP intentions.
- On a WiFi network you may find that only some MAC addresses are allowed by the access points, so you can borrow one of them taking care o to use it when the owners are online.
- During several pen-testing acts you may need to create specific MAC addresses, or discard used ones for new ones.
- As I said before, some licensing schemes consider your MAC as the unique identifier to bind a specific license. I would normally say you must not use this method to bypass some sort of licensing, but since it is very stupid it may be an incentive for people to find better protection algorythms.
- You may spoof addresses on your devices to make it simpler to distinguish their traffic, for example when capturing traffic on busy networks (you can create "your own" OIDs).
- You can just want a MAC that is easy to remember (or funny, just google for those).
- Your suggestion here...
Usage
This is a simplified version compared to the original one, but the basic task are accomplished in the same way. The interface is pretty simple: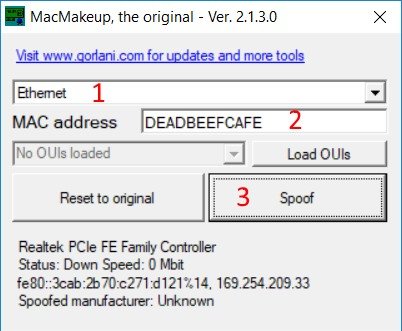
To spoof your MAC address you just need to:
1. Select your network interface
2. Type the new MAC address into the box
3. Click "Spoof"
Done! You just need to disable and enable the interface again.
If the MAC is already spoofed on an interface you can use the "Reset to original" button to go back to your original one.
Command line (scripted) usage
Since versions 2.2.x you can use MacMakeup from the command line. You can automate tasks like having a new MAC at each boot, or switch from one MAC to the other in a click or following events. For example the Windows scheduler allows you to execute script based on a lot of events.When using scripting the GUI interface does not show up if not for critical errors, any output will be directed to a macmakeup.txt file created in the same directory the executable resides. So you must have permission to write to that directory (do not put it in Windows32!).
You just start MacMakeup with some command line arguments. Valid ones are:
- list: writes the list of available interfaces to the macmakeup.txt file. The list contains the interface
GUID and the description. It is something like:
{6A4464B2-0FF4-4D69-B0E3-6D7DC289C41B} Bluetooth Network Connection
{B42E9999-20A5-4F43-B12B-B7670A0D4214} Local Area Connection
{0FF40FF4-20A5-4D69-B12B-B0E3B0E3B0E3} WiFi adapter
The part between with the {} is the interface ID we need in the other commands. -
set <interface ID> [NEW_MAC]: sets (spoofs) the new MAC address.
The first parameter is the interface ID from the list command.
The MAC address part is (partially) optional. You can type a partial MAC address, for example 005056 (VMWare). In this case the remaining part of the MAC is randomly generated. There is no minimum or maximum number of digits you must pass as the parameter, so if you just type the OUI of VMWare MacMakeup will generate the host part, if you go further and pass 00505612 only the last 4 digits will be appended. If you do not type anything at all a completely random MAC is generated.
Examples:
MacMakeup.exe set {0FF40FF4-20A5-4D69-B12B-B0E3B0E3B0E3} 005056 (generates a VMWare MAC address)
MacMakeup.exe set {0FF40FF4-20A5-4D69-B12B-B0E3B0E3B0E3} 12345678 (generates a MAC address starting with 12345678)
MacMakeup.exe set {0FF40FF4-20A5-4D69-B12B-B0E3B0E3B0E3} (generates a fully random MAC address)
-
reset <interface ID>: resets the MAC address to the factory one
Examples:
MacMakeup.exe reset {0FF40FF4-20A5-4D69-B12B-B0E3B0E3B0E3}
OUI management
Starting from 2.1.x the distribution zip contains an oui.txt file. The file is a stripped version of the one you can download here. This file is a sort of database that maps the first 24 bits of the MAC address to a manufacturer. For example if you see a MAC starting with 00A03F you can assume it is from a device that was made by Apple. This if there were no spoofed MAC addresses of course.Loading (and working) with the OUI database is not mandatory and can slow down the program, so load them if needed by pressing "Load OUIs".
With the database loaded you can just select a manufacturer from the list and a new MAC address from that vendor will be proposed in the MAC address box. Also if you select and interface witha spoofed MAC, the presumed vendor will be displayed in the information area.
You can type part of the name of the desired vendor in the box to filter the database.
If you do not need all of the (about) 30000 manufacturers, you can reduce the file to the bunch you use most, just delete the lines you don't need. Keep in mind that only the lines containing "base 16" are needed. You can easily update the file running:
curl -o - http://standards-oui.ieee.org/oui.txt | grep "base 16" > oui.txt
If you only need to spoof VMWare addresses you can modify the above command as:
curl -o - http://standards-oui.ieee.org/oui.txt | grep "base 16" | grep VMWare > oui.txt
You got the picture. Remember, the smaller the file, the faster the loading.
Starting from 2.2 the list was further reduced to 12k elements, so if you need the complete one just use the instructions above.
Permissions
You can launch the application with non administrator rights: in this case you can check the status of the interfaces and see which ones are have spoofed MAC.To change a MAC address you need to start the application with administrative rights. Those rights are also needed to disable and then enable the interface.
Platforms
This application runs on Windows platforms having the .NET framework 3.5 installed. It was tested on Windows 7, Windows 10, Windows 2008, Windows 2012 and Windows 2016. If you tested one platform, drop me a note.License and disclaimer
This software is completely free, use it at your will. If you include it in some project or publish it on your web site just drop me a note.There is no warranty the program will work on your computer, and no assurance it will not create a black hole or some other fancy disaster. Use it at your own risk.
Of course do not use it to do anything evil.
Version history
2.1.3.0: added OUI support2.2.3.1: added command line switches to automate spoofing
2.2.3.5: minor bug fix